iLocker™ Secure Notes
Lock your Notes and Keep them Private

Featured in:
Write Notes securely and with ease.
The new iLocker™ Secure Notes App, makes it easy and implements the highest level of security to write private notes, and even record voice memos.
All personal notes are automatically encrypted, can be clearly organized, and assigned to individual categories. In this way, the importance of a written note can also be quickly captured in color.
-
AES-256
-
Dictation Machine
-
Self-Destruction
-
Deep Detective™

AES-256 bit Encryption. Military style.
iLocker™ Secure Notes is a powerful encryption app that encrypts your notes using the 256 bit AES (Advanced Encryption Standard) algorithm. This encryption technology is one of the most impregnable available today and is used to encrypt top secret government, industrial and military documents.
The encryption process is carried out right in your device, and its symmetrical cryptography guarantees that your notes can be only accessed by you.
Safe dictation machine:
Record important moments
The integrated dictation machine is the ideal companion to securely record important moments. It can be used as a regular voice recorder to record voice memos, business meetings, interviews, lectures, and more.
The minimalistic design allows easy usability, and offers a high-quality recording experience.

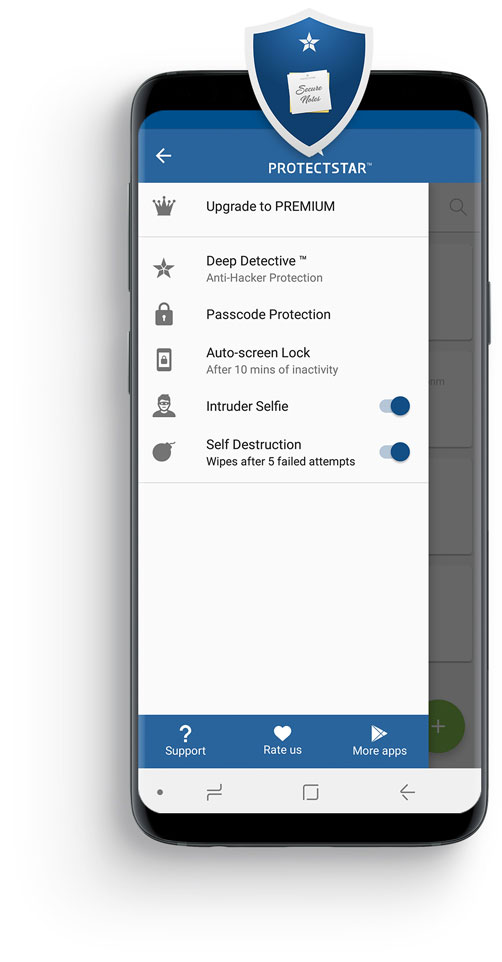
In case of emergency: self-destruction
Even in an emergency, your private notes and voice recordings are safe. If the Android smartphone gets lost or stolen, all data will be automatically destroyed after 5 invalid password attempts.
This not only deletes the data, but also securely erase the entire note safe with certified deletion algorithms. The extinguishing technologies for this feature, comes from the award-winning and popular iShredder™.
A smart hacker protection:
Deep Detective™
In 2016, with Deep Detective™ we have created an intelligent detective, who monitors all access - similar to a firewall - only much smarter.
In iLocker™ Secure Notes, the Deep Detective™ protection module permanently controls which process is currently accessing the encrypted data of your notes safe. It also reports known (and thanks to modern heuristic methods) it also reports unknown attacks.
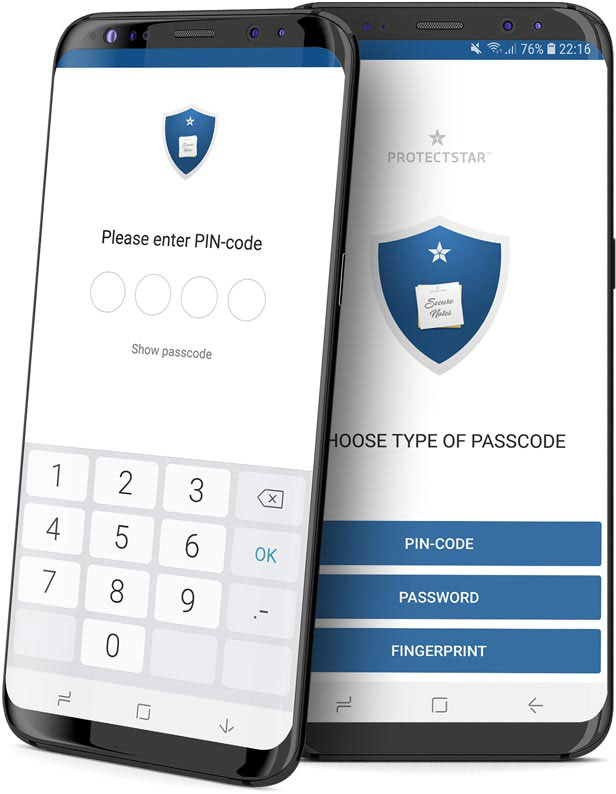
Guaranteed: No backdoors
The data is encrypted directly on the device, and symmetrical cryptography guarantees that only the user himself can access his notes. Without or forgotten password, the notes can no longer be accessed or the private data decrypted. In addition, the passcode is not stored on the device.
ProtectStar™ guarantees that no backdoors or master passwords are hidden in iLocker™. For reasons of transparency, the symmetric encryption algorithm used is provided as a download for your own analysis.
package com.protectstar.ilockersecurenotes.encryption
import com.protectstar.ilockersecurenotes.utils.StringUtils
import java.security.GeneralSecurityException
import java.security.Key
import java.security.SecureRandom
import javax.crypto.Cipher
import javax.crypto.spec.IvParameterSpec
import javax.crypto.spec.SecretKeySpec
class Encrypter(val secretKey: String, seedValue: String) {
@Throws(CryptoException::class)
fun encrypt(data: String): String {
val dataBytes = StringUtils.toBytes(data)
val key = generateKey()
// Create random initialization vector.
val initVector = ByteArray(IV_LENGTH)
_secureRandom.nextBytes(initVector)
val encryptedBytes: ByteArray
try {
val cipher = Cipher.getInstance("AES/CBC/PKCS7Padding")
cipher.init(Cipher.ENCRYPT_MODE, key, IvParameterSpec(initVector))
encryptedBytes = cipher.doFinal(dataBytes)
} catch (ex: GeneralSecurityException) {
throw CryptoException(ex)
}
// result is initVector + encryptedBytes.
val result = ByteArray(initVector.size + encryptedBytes.size)
System.arraycopy(initVector, 0, result, 0, initVector.size)
System.arraycopy(encryptedBytes, 0, result, initVector.size, encryptedBytes.size)
return StringUtils.toBase64(result)
}
@Throws(CryptoException::class)
fun decrypt(data: String): String {
val dataBytes: ByteArray
try {
dataBytes = StringUtils.fromBase64(data)
} catch (ex: IllegalArgumentException) {
throw CryptoException("base64 failed to decode.", ex)
}
if (dataBytes.size < IV_LENGTH) {
throw CryptoException("Value to decrypt is too short.")
}
val key = generateKey()
try {
val cipher = Cipher.getInstance("AES/CBC/PKCS7Padding")
cipher.init(Cipher.DECRYPT_MODE, key, IvParameterSpec(dataBytes, 0, IV_LENGTH))
return StringUtils.toString(
cipher.doFinal(dataBytes, IV_LENGTH, dataBytes.size - IV_LENGTH))
} catch (ex: GeneralSecurityException) {
throw CryptoException(ex)
}
}
@Throws(CryptoException::class)
private fun generateKey(): Key {
return SecretKeySpec(
CryptoUtils.P_SHA256(StringUtils.toBytes(secretKey), StringUtils.toBytes(secretKey),
16), "AES")
}
companion object {
private val IV_LENGTH = 16
private val _secureRandom = SecureRandom()
}
}
package com.protectstar.ilockersecurenotes.encryption
import java.security.InvalidKeyException
import java.security.NoSuchAlgorithmException
import javax.crypto.Mac
import javax.crypto.spec.SecretKeySpec
internal object CryptoUtils {
@Throws(CryptoException::class)
fun P_SHA256(secret: ByteArray, seed: ByteArray, required: Int): ByteArray {
var required = required
val mac: Mac
try {
mac = Mac.getInstance("HmacSHA256")
} catch (ex: NoSuchAlgorithmException) {
val errMessage = "Error in createTokenSecret: " + ex.localizedMessage
throw CryptoException(errMessage, ex)
}
val out = ByteArray(required)
var offset = 0
var tocpy: Int
var A: ByteArray
var tmp: ByteArray
A = seed // A(0)
while (required > 0) {
val key = SecretKeySpec(secret, "HMACSHA256")
try {
mac.init(key)
mac.update(A)
A = mac.doFinal() // A(1)
mac.reset()
mac.init(key)
mac.update(A) // A(1)
mac.update(seed)
tmp = mac.doFinal() // HMAC_SHA-256(secret, A(1) + seed)
tocpy = min(required, tmp.size)
System.arraycopy(tmp, 0, out, offset, tocpy)
offset += tocpy
required -= tocpy
} catch (ex: InvalidKeyException) {
val errMessage = "Error in P_SHA256: " + ex.localizedMessage
throw CryptoException(errMessage, ex)
}
}
return out
}
/**
* @return The minimum of two int values.
*/
private fun min(a: Int, b: Int): Int {
return if (a > b) b else a
}
}
package com.protectstar.ilockersecurenotes.encryption
import android.content.Context
import com.protectstar.ilockersecurenotes.NoteApplication
import com.protectstar.ilockersecurenotes.utils.BitmapUtils
import com.protectstar.ilockersecurenotes.utils.FileUtils
import io.reactivex.BackpressureStrategy
import io.reactivex.Flowable
import java.io.File
import java.io.FileOutputStream
import java.io.FileInputStream
interface MediaEncrypter {
fun encryptImage(filePath: String, reqWidth: Int, reqHeight: Int): Flowable
fun decryptImage(encryptedFilePath: String): Flowable
fun encryptAudio(filePath: String): Flowable
fun decryptAudio(context: Context, filePath: String): Flowable
}
class Base64MediaEncrypter(val encrypter: Encrypter) : MediaEncrypter {
override fun encryptImage(filePath: String, reqWidth: Int, reqHeight: Int): Flowable {
return Flowable.create({ emitter ->
val fileName = "${System.currentTimeMillis()}.enc"
val bitmap = BitmapUtils.loadBitmapFromFile(filePath, reqWidth, reqHeight)
val base64 = BitmapUtils.encodeToBase64(bitmap)
val encrypted = encrypter.encrypt(base64)
val path = writeToFile(NoteApplication.instance, encrypted.toByteArray(), fileName)
emitter.onNext(path)
emitter.onComplete()
}, BackpressureStrategy.BUFFER)
}
override fun decryptImage(encryptedFilePath: String): Flowable {
return Flowable.create({ emitter ->
val fileName = FileUtils.getFileNameWithoutExtension(encryptedFilePath)
val base64 = readFromFile(encryptedFilePath)
val decrypted = encrypter.decrypt(base64)
var result = ""
if (decrypted.isNotEmpty()) {
val bitmap = BitmapUtils.decodeFromBase64(decrypted)
val tempDir = NoteApplication.instance.cacheDir
val outputFile = File.createTempFile("$fileName-", ".png", tempDir)
BitmapUtils.saveBitmap(outputFile, bitmap)
result = outputFile.absolutePath
}
emitter.onNext(result)
emitter.onComplete()
}, BackpressureStrategy.BUFFER)
}
override fun encryptAudio(filePath: String): Flowable {
return Flowable.create({ emitter ->
val fileName = "${System.currentTimeMillis()}.enc"
val base64 = FileUtils.encodeToBase64(filePath)
val encrypted = encrypter.encrypt(base64)
val path = writeToFile(NoteApplication.instance, encrypted.toByteArray(), fileName)
emitter.onNext(path)
emitter.onComplete()
}, BackpressureStrategy.BUFFER)
}
override fun decryptAudio(context: Context, filePath: String): Flowable {
return Flowable.create({ emitter ->
val fileName = FileUtils.getFileNameWithoutExtension(filePath)
val base64 = readFromFile(filePath)
val decrypted = encrypter.decrypt(base64)
var result = ""
if (decrypted.isNotEmpty()) {
val audio = FileUtils.decodeFromBase64(decrypted)
val tempDir = NoteApplication.instance.cacheDir
val outputFile = File.createTempFile("$fileName-", ".m4a", tempDir)
writeToFile(audio, outputFile.absolutePath)
result = outputFile.absolutePath
}
emitter.onNext(result)
emitter.onComplete()
}, BackpressureStrategy.BUFFER)
}
private fun writeToFile(context: Context, data: ByteArray, fileName: String): String {
val path = context.filesDir
val file = File(path, fileName)
if (!file.exists()) {
file.createNewFile()
}
val stream = FileOutputStream(file)
stream.use { it.write(data) }
return file.absolutePath
}
private fun writeToFile(data: ByteArray, filePath: String): String {
val file = File(filePath)
if (!file.exists()) {
file.createNewFile()
}
val stream = FileOutputStream(file)
stream.use { it.write(data) }
return file.absolutePath
}
private fun readFromFile(path: String): String {
val file = File(path)
if (!file.exists()) {
return ""
}
val length = file.length().toInt()
val bytes = ByteArray(length)
val inputStream = FileInputStream(file)
inputStream.use { it.read(bytes) }
return String(bytes)
}
}
The app is free and with one In-app-purchase
you can get all Premium features
-
Write private Notes with the highest level of safety
-
Integrated voice (dictation) recorder
-
Notes and Voice memos are encrypted with AES-256 bit incredible military encryption
-
Amazing organization and sorting of notes
-
The importance of a written note can also be quickly captured in color
-
In case of emergency: self-destruction after 5 invalid password attempts
-
Guaranteed no backdoors or master passwords! Open Source code of the symmetric encryption algorithm provided as download
-
Automatic display protection
-
24/7 Support via e-Mail from our Support Heroes
-
PREMIUM: Deep Detective™ protection module detects unknown attacks, even within the notes vault
-
PREMIUM: Extended Hacker Protection with Intruder Selfie feature
-
PREMIUM: Store unlimited Notes and Voice Memos